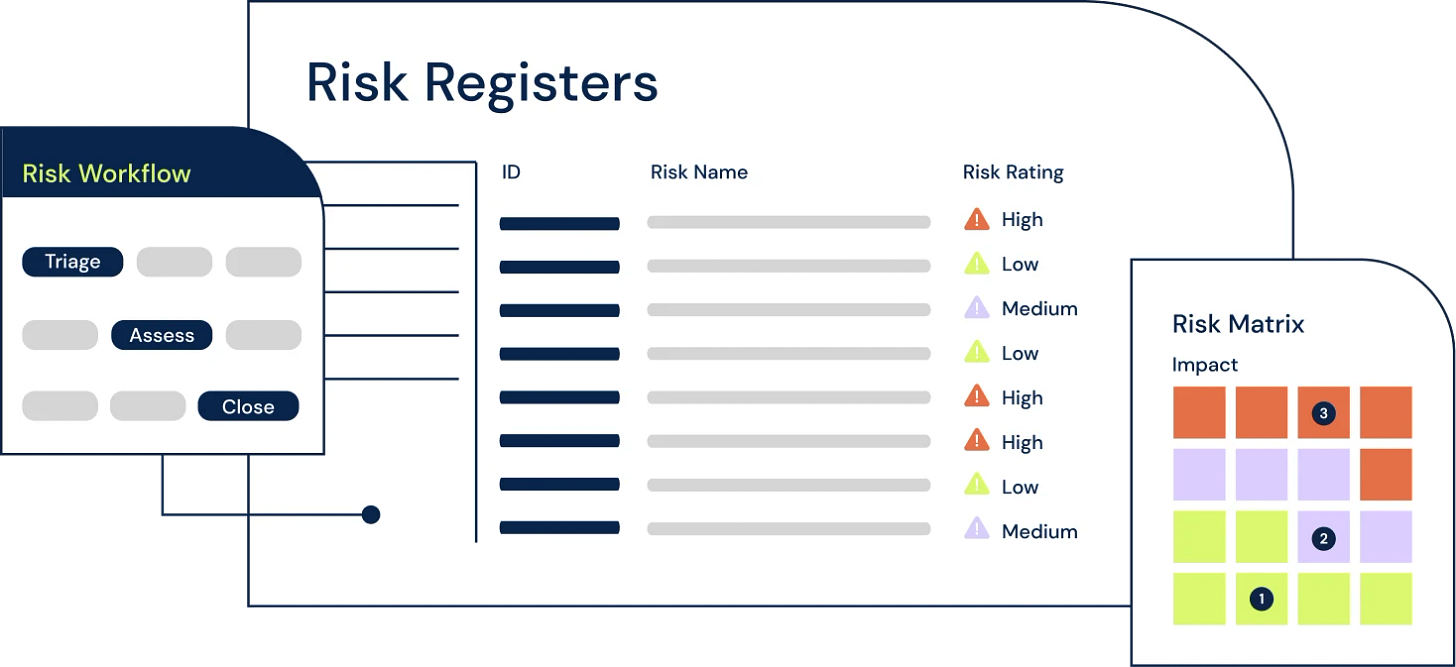
Definition
A risk register is a document that records all of your organisation's identified risks. It also has:
the likelihood and consequences of a risk occurring
the actions you are taking to reduce those risks
who is responsible for managing them
Importance
A risk register is the most common way to conform with Clause requirements 6.1.1 and 6.1.2. Without a risk register or appropriate alternative, your business could receive a major non-conformity when trying to attain an ISO 27001 certification.
From a non-compliance perspective, it centralises your organisation’s approach to dealing with important risks. Without it, this can leave room for risks to be unattended which increases the business’s susceptibility to being hacked.
Application
There are several options when trying to create a cybersecurity risk register:
Use a security governance tool such as Vanta - security governance or GRC tools provide organisations with lots of features that streamline compliance. One of these features is an in built risk register with template risks for the business to choose from.
Find online templates - There are many risk register templates available online for businesses to use. Some examples include Secureframe or ISO-Docs.
Enjoyed this Article?
Subscribe using the button below for more cybersecurity content!
Feel free to connect with me on LinkedIn for more cybersecurity discussions. You can also reach out via email if you have any questions or feedback.
Have a good day and stay cyber safe!
References
Disclaimer
This newsletter is intended solely for the purpose of providing security awareness and general information related to cybersecurity. The content presented here is for educational and informational purposes only. It should not be considered as personalised security advice or a solicitation for specific security services.
Every organisation and individual's cybersecurity needs and circumstances are unique. For personalised security recommendations or services, we strongly advise consulting with a qualified cybersecurity professional or seeking guidance tailored to your specific situation.
While we strive to ensure the accuracy and reliability of the information presented in this newsletter, we make no warranties or representations, express or implied, regarding the completeness, accuracy, or suitability of the content for contextualised security initiatives. We shall not be held responsible for any actions taken or decisions made based on the information provided in this newsletter.
Readers are encouraged to exercise their own judgment and due diligence when implementing security measures or making cybersecurity-related decisions.
If you have any questions or require personalised cybersecurity assistance, please consult with a qualified cybersecurity expert or seek professional advice tailored to your specific needs.