Definition
The contents of ISO 27001 is separated into:
ISMS Clauses
Annex A Controls
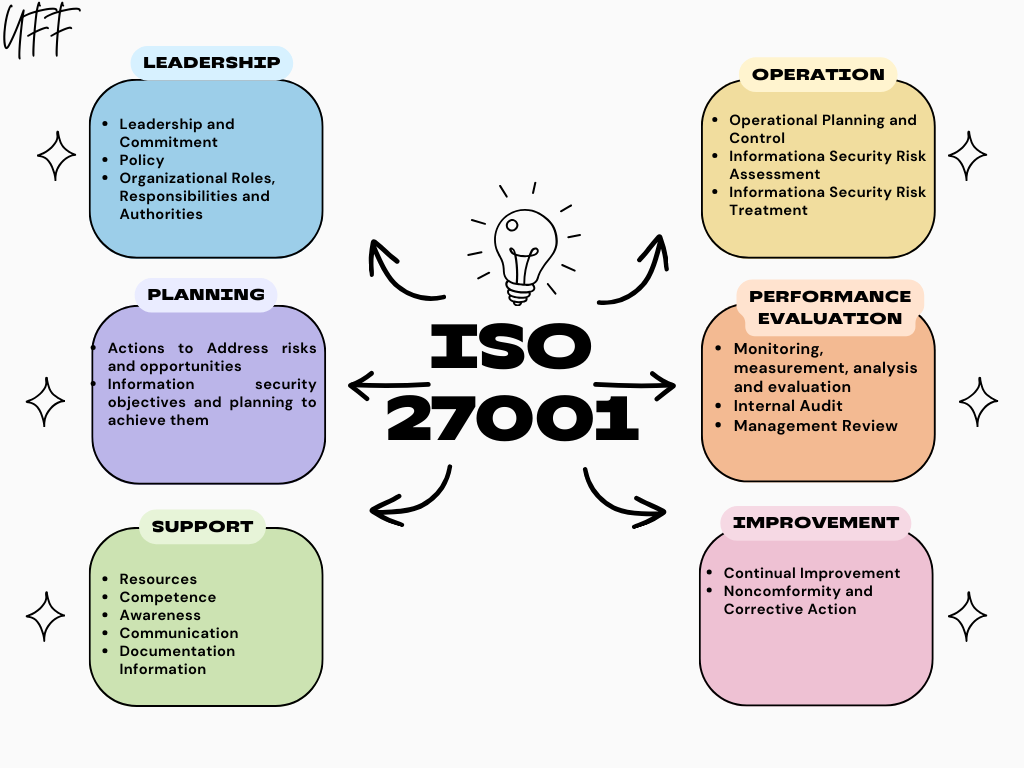
The ISMS clauses include 11 clauses that define the baseline documentation that your firm needs to run an ISMS according to ISO 27001. Out of these, only clauses 4-10 are mandatory for an organisation.
Annex A Controls are a wide selection of security measures or ‘controls’ you can implement to mitigate identified risks during your initial risk assessment. There are 93 controls in the latest version of ISO 27001:2022.
These controls are separated into the risks they address:
Organisational Controls - These controls pertain to the documentation established within an organisation to manage and protect information assets. This includes roles and responsibilities, access control policies, and incident response procedures.
People Controls - These mitigate the risks of employees intentionally or unintentionally contributing to a cyberattack. For example:
training programs to educate employees on cybersecurity best practices. This reduces their susceptibility to threats such as phishing attacks.
conducting background checks to determine their inclination to unethical behaviours such as stealing sensitive data.
Physical Controls - Physical controls are measures implemented to secure physical assets and facilities that house sensitive assets and data. These measures may include locks, biometric systems, and surveillance cameras.
Technological Controls - These refer to the use of technological solutions to protect information assets and mitigate cybersecurity risks. This includes implementing firewalls and antivirus software.
Importance
If the mandatory clauses are not in place, this will suggest to an auditor that the ISMS hasn’t been sufficiently set up to maintain the organisation’s security.
Therefore, an incomplete setup of the ISMS will diminish the effectiveness of any Annex A controls being implemented.
Application
To effectively set your ISMS and associated controls, it is recommended to choose one or both of the following:
Use a security Governance, Risk and Compliance (GRC) tool - Security GRC tools such as Vanta, or SecureFrame have resources to automate part of the ISO 27001 compliance process for you. This is extremely helpful and efficient in the long run as it reduces the manual effort required to achieve and maintain your ISO 27001 certification.
Reach out to a cybersecurity professional - Cybersecurity professionals who specialise in GRC can make the ISO 27001 process much less intimidating and provide clear direction on what needs to be done. Ensure they have assisted multiple organisations in successfully attaining ISO 27001 so they speak from experience.
Enjoyed this Article?
Subscribe using the button below for more cybersecurity content!
Feel free to connect with me on LinkedIn for more cybersecurity discussions. You can also reach out via email if you have any questions or feedback.
Have a good day and stay cyber safe!
Disclaimer
This newsletter is intended solely to provide security awareness and general information related to cybersecurity. The content presented here is for educational and informational purposes only. It should not be considered as personalised security advice or a solicitation for specific security services.
Every organisation and individual's cybersecurity needs and circumstances are unique. For personalised security recommendations or services, we strongly advise consulting with a qualified cybersecurity professional or seeking guidance tailored to your specific situation.
While we strive to ensure the accuracy and reliability of the information presented in this newsletter, we make no warranties or representations, express or implied, regarding the completeness, accuracy, or suitability of the content for contextualised security initiatives. We shall not be held responsible for any actions taken or decisions made based on the information provided in this newsletter.
Readers are encouraged to exercise their own judgment and due diligence when implementing security measures or making cybersecurity-related decisions.
If you have any questions or require personalised cybersecurity assistance, please consult with a qualified cybersecurity expert or seek professional advice tailored to your specific needs.